I'm deriving keys from a user-supplied passphrase for symmetric encryption using AES-256 in CBC mode with a HMAC for authenticity/integrity.
My key derivation function currently looks like this:
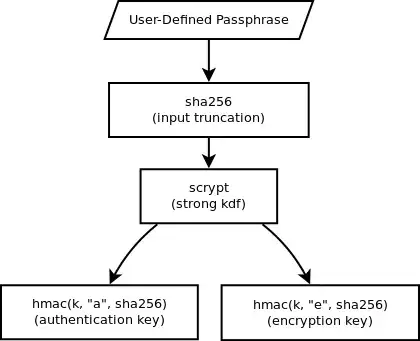
Please note that scrypt could just as easily be subbed out for PBKDF2 or bcrypt, that remains to be seen.
I have a couple questions:
- Does input truncation using SHA-256 expose any potential weaknesses?
- My reasoning for doing it in the first place is because many algorithms like bcrypt only accept a limited password input size. (bcrypt seems to accept up to 55 or 72 characters, not sure on the source of this)
- Would it be better to prefer a hash method with a longer output, ie SHA-512?
- When generating the HMAC authentication and encryption keys, would I benefit at all from using SHA-512?
- AES-256 IIRC needs 256-bit keys, so if I either used AES-192 or used SHA-512, how would I go about fixing the discrepancy in required size?