I try to understand the GCM-MODE used in TLS. The problem I have had is described below.
1:textbook describes how GHASH works:
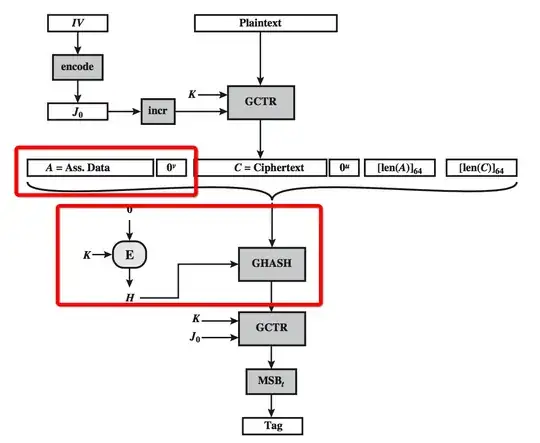
 2:
I get some debuginfo from openssl code that contain enc_key(32 bytes) and ADD(13 bytes).
2:
I get some debuginfo from openssl code that contain enc_key(32 bytes) and ADD(13 bytes).
I try to simulate the GCM MUL by coding like this:
static unsigned char buf[16]={0};
static unsigned char ctr[16]={0};
static unsigned char ectr[16];
static int poly[]={128, 7, 2, 1, 0, -1};
BN_GF2m_arr2poly(poly, p);
AES_set_encrypt_key(gcm_key, 256, &ghash_key);//gcm_key is derived from debug info
AES_encrypt(ctr, ectr, &ghash_key);
BN_bin2bn(ectr, 16, k);//construct K
memcpy(buf, gcm_add, sizeof(gcm_add));//gcm_add is a 13 bytes data derived form debug info
BN_bin2bn(buf, 16, a);//construct ADD
BN_GF2m_mod_mul(r, a, k, p, bnctx);//compute (add · K) as first part of computing tag
But the result r is different from the result in openssl code(The code use GCM_MUL).
I confirm that the gcm_add and gcm_key are correct and even the ectr encrypted by gcm_key is also correct compared to debug info from code.