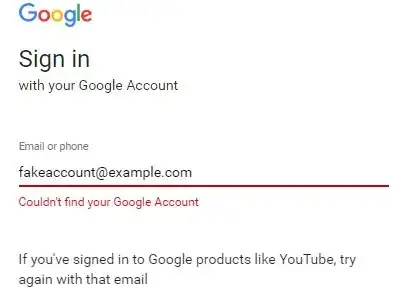
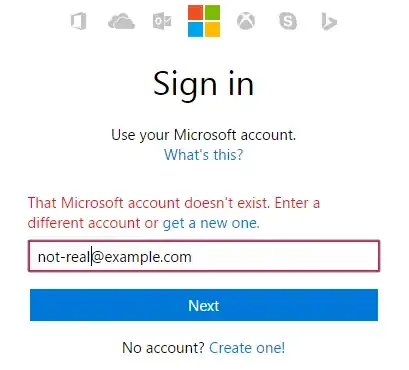
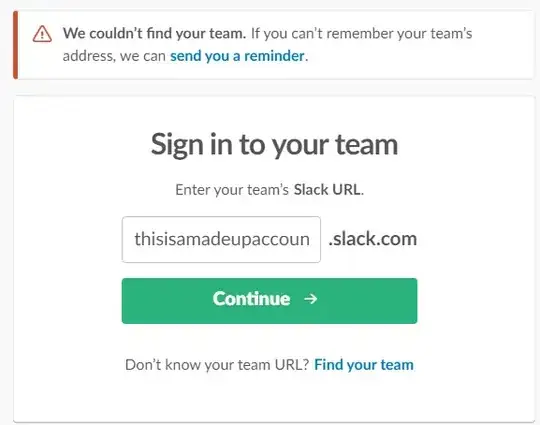
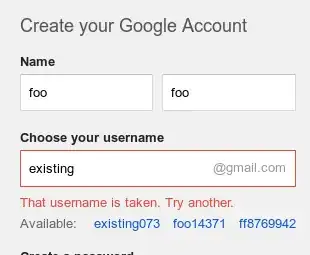
The purpose of not disclosing the active user identifier is to prevent enumeration of a large number of the accounts.
Strictly speaking, you could protect against this by allowing duplicate accounts, but this is a terrible design and will lead you to all kinds of trouble.
Another way you can do this is to assign users an identifier - constructing one that is unused. But this is such a poor usability experience that it might not be worth it *.
The sensible way to mitigate the risk is to implement any anti-enumeration feature - for instance, a good quality captcha, to slow down any enumeration attempt. Then the design is reasonably safe.
The residual risk is then that you leave open the verification of one very high value account - for instance, barack.obama@gmail.com. Then you mitigate this risk by also implementing a control against password cracking attempts, etc.
* Salzer and Shroeder, The Protection of Information in Computer Systems, Section I.A.3)h) Psychological acceptability: It is essential that the human interface be designed for ease of use, so that users routinely and automatically apply the protection mechanisms correctly. Also, to the extent that the user's mental image of his protection goals matches the mechanisms he must use, mistakes will be minimized. If he must translate his image of his protection needs into a radically different specification language, he will make errors.