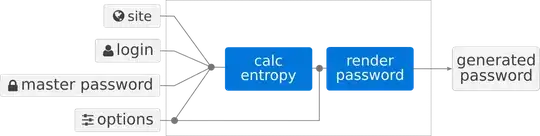
I am the creator of LessPass, a deterministic password generator.
The core of LessPass is not very complicated.
I have 2 methods calc_entropy and render_password:
calc_entropy transforms the master password + site + login into a very large integer that I call entropy (I don't know if it's the right term, but it represents my amount of randomness in my system). It uses pbkdf2 100k iterations.
render_password uses/consumes this entropy. I have a loop that comes to pick a character from a list of desired characters thanks to the remainder of a long division.
To be sure to have a char for each rule (lowercase, uppercase, digits, symbols) I always pick 1 character for each rule and I insert it in a pseudo-random way in the generated password.
The detail of the algo with an example is available here.
LessPass allows its users to save on a server profiles for their generated passwords to avoid remembering sites rules. A profile looks like this:
{
"login": "my_login",
"site": "www.exemple.org",
"lowercase": false,
"uppercase": false,
"symbols": false,
"digits": true,
"counter": 1,
"length": 6
}
I would like to introduce a new functionality by allowing the import of passwords from other password managers.
Imagine that my old password for www.example.org is foobar.
I can generate a very large number which after passing in the function render_password generated the password foobar (randomly generated entropy).
I would like to store in the password profile the difference between the actual entropy and a randomly generated entropy which goes through render_password generates foobar.
To generate the old password, I calculate the entropy, apply the diff then render the password.
I did a naive poc here
If you have read me so far thank you!
My question: to what extent do I increase the brutuceforcability of the master password if an attacker stole the LessPass database (he knows the diff) and stole the user's password (he knows foobar) compared just knowing the foobar password?