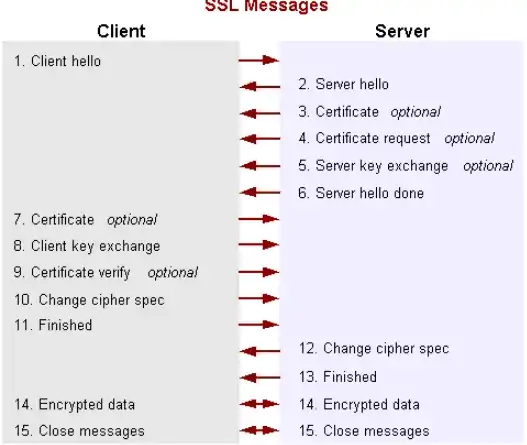
In below ssl diagram :
I have one doubt with 1-way ssl. If there is an interceptor in-between client and server who can alter in following way :
- In step 8, when client is sending his symetric key to server, encrypted by server's public key, if interceptor ignores client message, instead sends its own key using same server's public key. This was server will think that interceptor is actual client.
- In step 14, interceptor can ignore actual client data, instead he can generate its own data ( even HMAC) with its own key, and server will accept this request too, as server has interceptor's key only.
This way someone can always mock a client and sends its own data instead of actual client.
Since in 1-way ssl, we are not verifying client authenticity, can someone alter ssl by above way ? Am I missing anything big ?