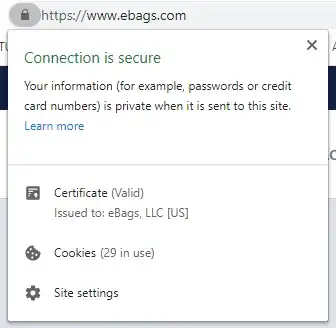
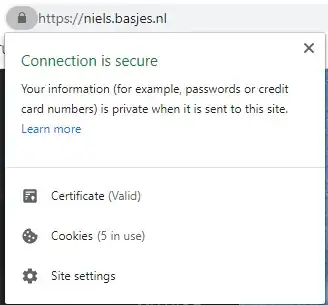
Years ago (~2010-2019) the Extended Validation (EV) Certificates made a lot of sense. The user in their browser would see a clear difference between
- a "grey" (http/not secured) website
- a "green lock" (https normal certificate) website
- and a "green lock with name of the company owning the website" (https ev certificate) website.
Back then having such a certificate meant that normal users would have a clear indication they are actually connected to the website they had in mind.
Today (~2021) in Chrome I no longer clearly "in your face" see the difference anymore between a website with a normal certificate (like my homepage) and a website with one. Knowing their existence I actually had a hard time finding a website that still has one.
So my question is in general: If there still any value for any website to have an EV certificate?