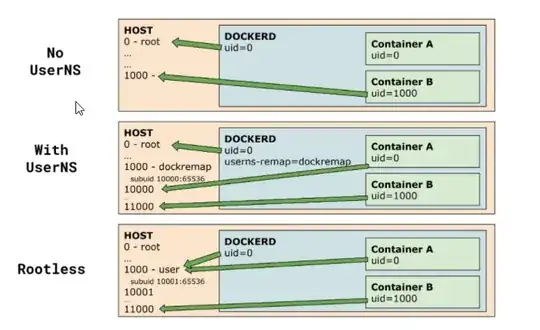
You can and generally should (1) run docker daemon (or podman, or something else) as rootless, and/or (2) use user namespace-remapping, to improve security.
You can also (3) use rootless images, where the container does not run any processes as root. For example, nginx-unprivileged runs as nginx user instead of root.
Sometimes the images do not have rootless variants, and creating a rootless variant for some tool X may involve non-trivial amount of work (solving problems with file permissions, etc).
If we already are using #1 and/or #2, does it matter if the image is not rootless?