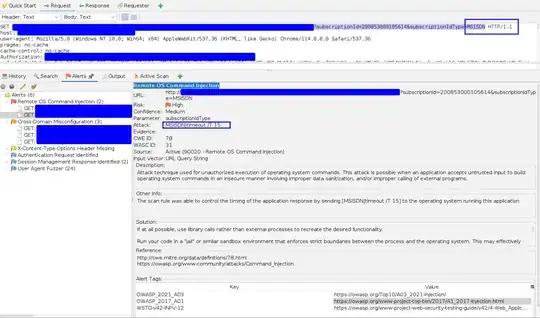
Using ZAP OWASP 2.13.0 and found a so-called "Remote command injection". But either in report or in Alerts the URL + query the URL does not contain attack string. Open the query in Request editor, the query is still correct.
Did the scan twice so maybe it's not temporary traffic jam. But I cannot reproduce it with manual test.
In scan, the request returns 200. But in my manual test with attack string, if not encoded:
GET /path?subscriptionId=200853000105614&subscriptionIdType=MSISDN|timeout /T 15 HTTP/1.1
The response body is html, not JSON though:
<html><body><h1>400 Bad request</h1>
Your browser sent an invalid request.
</body></html>
If encoded:
GET /path?subscriptionIdType=MSISDN%7Ctimeout%20%2FT%2015
It returns proper JSON with correct error message.
But in either case it's 400, not 200.
So:
- anyone knows how the real query should be? I only see the attack string, but putting it into the query(encoded or not) does not return 200; I see 400 error which is expected.
- Anyway to associate the alert with the query in History tab or Active Scan tab so I see what happened indeed?
BTW the application is based on an distroless image so I think running timeout on it will lead to executable not found error. Verified already, as there's no shell.
And, timeout /T is for Windows right? But the image is Linux based.