The router had briefly lost its WAN uplink. It's a “feature” in several manufacturers' routers and modems (specifically including Huawei, but others as well) to redirect you to the router's local "connection status" web page when there is no Internet connection, presumably to simplify the initial setup process (e.g. entering the SIM card's PIN without having to hunt for the gateway's IP address) or as an attempt to improve user experience.
Functionally it's the same as those public Wi-Fi networks which use the browser-based "captive portal" login process, which also involves MITMing and redirecting HTTP requests (to the extent that web browsers have learned to detect it, which probably made it more attractive for Huawei to implement this feature as well).
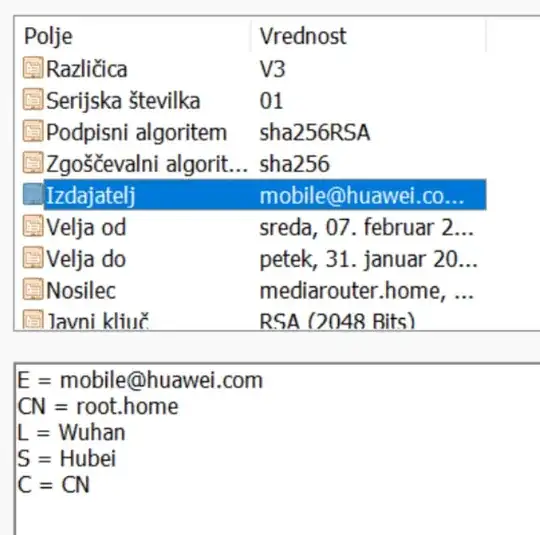
These are easy to distinguish based on the received certificate – a deliberately malicious MITM attack would at least have attempted to spoof the correct domain name in the 'Subject' field, whereas in a 'captive portal' setup, the certificate would just identify the gateway itself (and "mediarouter.home" is indeed what Huawei modems use).
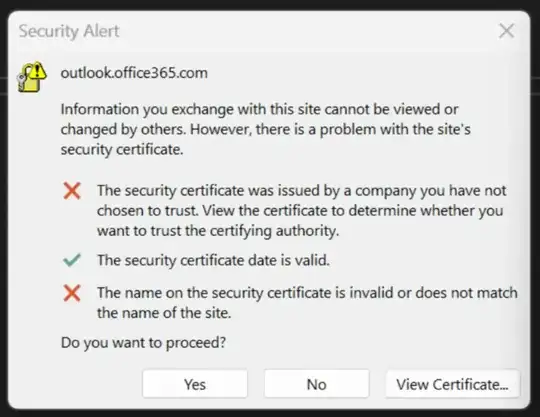
outlook.office365.com. It is statet above and in the first image. – gtu Dec 06 '23 at 20:10ipconfigandConnection-specific DNS Suffix . :is empty. – gtu Dec 08 '23 at 09:41