I am using college network to access internet. Many other users are using the same network. Recently I have been experiencing sluggish net connection. So when I did some investigation, I found that many other computers on the network have been sending ICMP packets to me. I used Wireshark to analyse the incoming packets . Here is an screenshot of my my analysis:
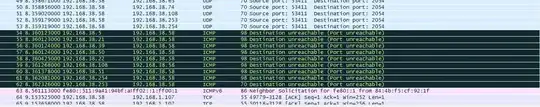
(My IP was 192.168.38.58)
The packet capture was filled with these ICMP request. When I searched the web about it then I found that there is an attack named smurf attack in which attacker force other system in the network to send ICMP request to victim system.
Is this an example of smurf attack? If so then how to prevent my computer from being Attacked.
Please provide solution for both linux and windows Operating system.
EDIT No. 1:------
When I changed the MAC address of my PC, everything got back to normal. No such malicious packets were observed.
EDIT No. 2:------
I had used Advanced Port Scanner to scan my active port.
The port which was sending UDP packet(53411) is closed
Can I use Wireshark on the school network?withNo.The part you quoted was merely an extension of that policy. I am not a school administrator so I can't really speak to the intent of such policies, but I do know they are common, and schools will take action. That being said school administrators aren't known for being very tech savvy, or reasonable when it comes to rule violations. In most cases it is advisable to get permission if you plan to use Wireshark on a University network. – Spaceman Spiff Jun 17 '15 at 21:27Users may not “sniff” networks or undertake comparable measures to obtain access to passwords or other information not made publicly available by the owner.I personally don't think that any University should have jurisdiction over what programs run on your computer, I am just warning anyone who may try this that I know there are Universities that do and are willing to enforce rules based on that. I'm not defending these Unis – Spaceman Spiff Jun 17 '15 at 22:20