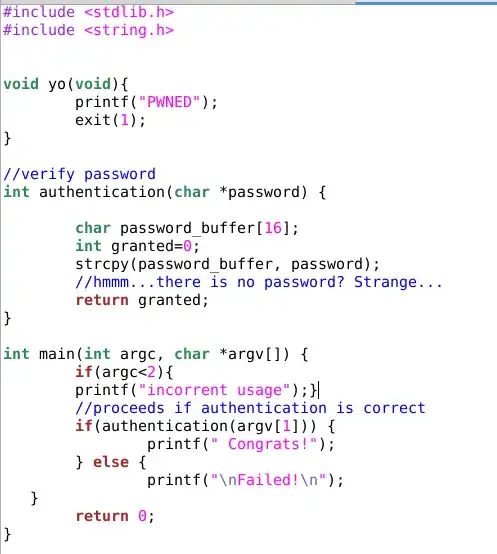
I was testing a simple C program with stack canary protection.
I attempted to bypass the protection by overwriting past the function's return address and overwriting main's address. I am overwriting it with the address of a function within the target program. I get the following result which leads me to believe an attack is possible:
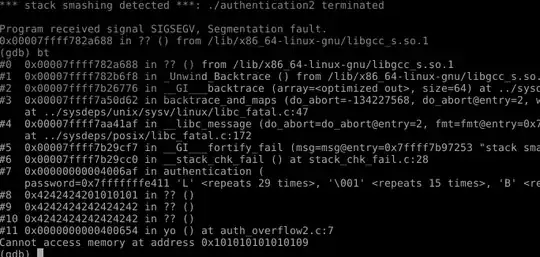
It detected the smash, but it looks like it attempted to jump into the target function, which is "yo". I attempted to manipulate whatever address it was attempting to access, but no luck.
My question is, is further exploitation possible? Is it terminating as a result of SIGSEGV (i.e. accessing 0x1010...) or the canary detection?
The idea came from this article
The program: