i recently received the following (rather obvious) phishing email:
i'm not a PayPal user so this particularly un-alarming for me. however, when viewing as plain text, it became evident that there were hidden characters between every displayed letter of each word, as so:
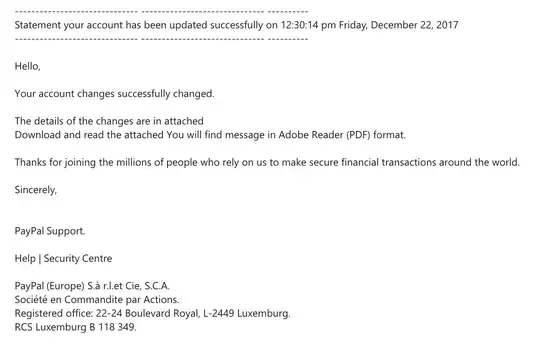
------------------------------ ------------------------------ ---------- Statement your account has been updated successfully on 12:30:14 pm Friday, December 22, 2017
HzeglelMo,
YmocuTr aMcacdoduvnbt cfhoannlgze1s sHuzcocXeysVsmfEudlIlKy cwh9a2nOgVead.
TFhFe dHePt2aNi2lGs oZf thhte cThzaAnAgJe3s abr9e iIn aztbteaVcshsegd DLorwCnIlFo6ald aYn0d rgeuaid tchGe altjtFaScMhJepd YZobu w3inlWl fOiAnFd m5edsDs0aHgJe iQn A2dToebee RgefaEdAenr (kPyDKFV) AfwoHr1mraMtn.
TuhsaunxkWs fjorr jXori1neienRg t6hKe mkimlAlci4oKn6s off pkeiospslLe w8h8o rIeGlDy oSn uNs tho mpatkEe s4e2csu3rie fFiqnNaXnsccikaEl thrtaEnOsia2cFt6iWocn2s a7rUoPuTned tLh1e wIoxr5lnd0.
SIiTnocAefrSeVlWyd,W
PVacy6Pka1l1bidttS0u4pjp0oErCtE.k
HbeUlrp r|xddl8vSme5cKu6rQi8tcyoslnnfCte8nrtDrDe
PcavyqPzaDlkix8tt(yEGuIrRodp9eP) S.à ri.jlH.IeSt C3i2ee, Sb.rC8.EAp.M SyobcHiété eOn CqoGmImwaBnmdhiYtfe plaAr AacNtkiIonXs. RoeSgPirsNtpe6rreWd oefGfJi1cteD: 212w-t2P4 BloJuJl5ejvBaYrmd R6oGykahl, Ls-c2S4r4r9 Lzulx1etmbb7u9rkg1. RKCHS LmuFxweCmUbyuLrmg BE 161t8 3V419a.
what could this be for? has anyone ever seen this?
UPDATE - here are the From + Subject headings
From: service@intl.paypal.com .
Sent: Sunday, December 24, 2017 9:39 PM
Subject: Case ID Number PP-M-LL0PUG4V : Statement your account has been updated successfully on 12:30:14 pm Friday, December 22, 2017