I'm trying to create a DFD for a threat modeling exercise. How much detail should I get into?
The SDL Threat Modeling guidelines state that I know that my DFD needs more detail when there is still a trust boundary in the DFD. Suppose there is a trust boundary between the datastore A and process B. Since there's a trust boundary, I know the DFD is not detailed enough. How can I go deeper, deep enough that no trust boundary is left? If I drill deeper into the process B and decompose it into smaller parts, will it always be possible to eliminate the trust boundary?
I have CRUD Operations on a database in my dataflow diagram, do I need to create 4 distinct dataflows to accomodate the needs or can I mark the dataflow with "CRUD Operation"?
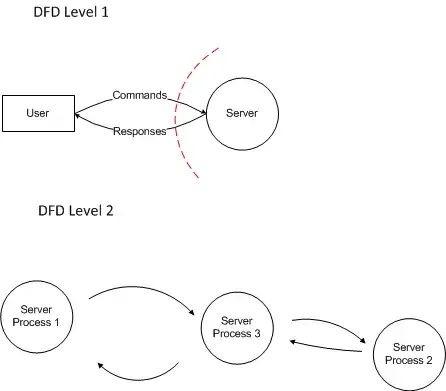
My question is how can I go deeper into other DFD level and omit the Trust Boundary. If I go deeper into the process B can I omit the Trust Boundary which is present on the more general level?
– theXs Apr 16 '13 at 07:37